Security
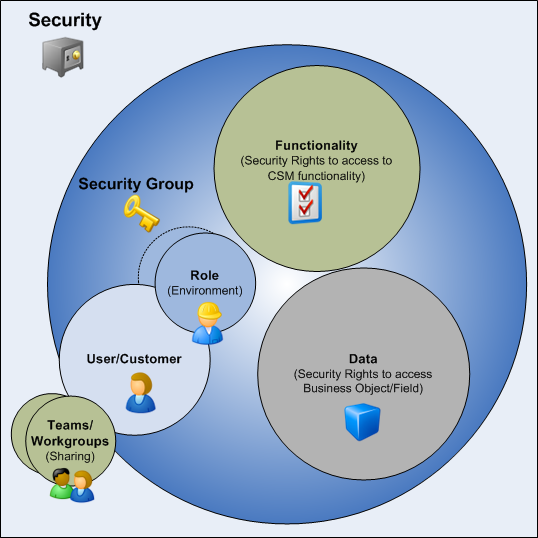
Security components include:
- Security Group: A Security Group is at the heart of CSM security. A Security Group is a collection of CSM security rights that controls access to CSM functionality and data (Business Objects/fields). Each User/Customer is assigned to only one Security Group. The User/Customer then inherits the security rights of that Security Group, as well as access to the Roles assigned to the Security Group. Examples of Security Groups include Admin, IT service desk manager, and Portal End-User.
- Role: A Role is a User/Customer's current function/responsibility in CSM, and controls how data is presented in that person's CSM environment. For example, a Role determines which Home Dashboard is displayed and how the Incident form looks (example: Which fields are exposed, required, etc.). A Role is assigned to a Security Group and can be assigned to more than one Security Group at a time. A User/Customer can access any of the Roles in his Security Group, but can only log in using one Role at a time. Examples of Roles include Service Desk Manager and Portal Customer.
- User: A User is a service desk professional who logs in and uses CSM to manage service desk data (example: A technician, manager, designer, system administrator, etc.). A User is assigned to only one Security Group (so they can access specific functionality and data), can log in using one or more Roles (so they can have a personal viewing environment), and can belong to one or more Teams (so they can share CSM items, such as Dashboards).
- Team: A Team is a collection of CSM Users that can share CSM items (such as Dashboards), record ownership, and assignments. Examples include Support, Management, and Knowledge Management. A Team plays an important part in record ownership because members of the Team can have additional rights to view and edit records.
- Customer: A Customer is an End-User, either an internal employee or an external individual, who relies on CSM to initiate/fulfill a Service or Product (example: A person reporting a lost password or requesting a new phone). If configured, a Customer can access CSM data and perform self-service activities using the Portal. A Customer is assigned to one, and only one, Security Group (so they can access specific functionality and data) can log in using their default Role (so they can have a personal Customer View) and can belong to one or more Workgroups (so they can share CSM items, such as Dashboards).
- Customer Workgroup: A Workgroup is a collection of CSM Customers who can share CSM items (such as Dashboards). Examples include Sales, HR, and Operations. A Workgroup plays an important part in record ownership because members of the Workgroup can have additional rights to view and edit records.
CSM provides an OOTB security design (complete with Security Groups, Roles, Teams/Workgroups, and system security settings). Implement this OOTB design (and just add Users/Customers, assigning them to other OOTB Security Groups, Roles, and Team/Workgroups), edit it, or create a new security design.
